Android App, Android Development and Security Advisory
Fledgling Developers' journey on Android App, Android Development and Security Advisory
Zero Permission App
How to verify an App is really Zero Permission and Safe?
Before you download an app from Play Store, you could select the "View details" under Permissions in the app store listing. If an app has no permission required you will see something like:
 |
| Picture of an app with no permission |
If you want a further test, you could use the free web service Exodus Privacy. You just need the app package name that you could get from a browser as shown:
 |
| Highlighted portion is the app id |
Enter the app id into the Exodus, and click "Perform analysis". After a short period of time, depending on the size of the app, a report will be generated for your viewing. An example is as shown:
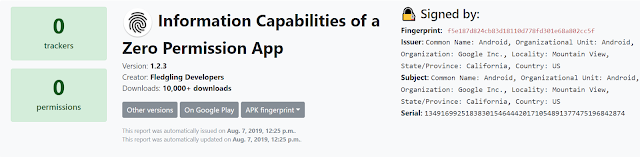 |
| Report on our Zero Permission App - Device Info |
The above are some simple checks that you could do, free and freely, for any app in the Play Store.
Hope this is helpful to someone out there. cheerios
Subscribe to:
Comments (Atom)


