Secure your secret notes with AES-256 encryption with this Zero Permission App
This app encrypt your notes into the very depth of internal storage in your device. The notes will stay in your phone and will not leave your phone. The encryption used for securing your notes is AES-256, refer to https://en.wikipedia.org/wiki/Advanced_Encryption_Standard, one of the strongest encryption scheme. Each note you type into Secret Notes AES-256 are encrypted. Your encryption key, or password, is not stored in any form in your phone or anywhere else.
Typical use cases: travelling to foreign countries, prying siblings, secret diary, too many passwords to remember, your very personal details such as bank a/c, financial statements
Typical use cases: travelling to foreign countries, prying siblings, secret diary, too many passwords to remember, your very personal details such as bank a/c, financial statements
Compare Secret Notes AES-256 With Other Secret Notes Apps in Google Play
Our Ten Strengths:
- No ads - which may or may not affect security, at least it annoys users when they are typing some secrets
- No network connectivity - Rather than trust anyone who tell you your data is safe, we mean it when there is no possible way for your data to leave our app
- No permission required for external storage media - this means we cannot copy your notes into some unintelligible form for later extrication
- We use the strongest encryption method available, specifically CBC-AES-256 with IV size 16, this can be audited
- We do not store your password (or password hash) anywhere in the app or in your phone. We just do not store your password but use a innovative method to verify the password is correct.
- You can verify the encrypted form of your notes, it can be audited
- This app does not have in-app billing so that we do not have to connect to any servers, including Google or any other Web Services
- This app will not send any notification to you because it cannot use the network functions and there is no reason for the app to send any notification
- This app does not use Fingerprints or Swipe Patterns to unlock your notes because these two methods cannot be implemented safely (more on this in future blogs) for this kind of app
- We take care of advance attacks such as dump and analysis of memory , app cache, code injection, and app tampering
We have started Zero Permission App (ZPA) initiative on our website. Zero permission app is an initiative to provide peace of mind to users by aiming to have no (ZERO) required permissions in Android, but still providing innovative and effective features to you.
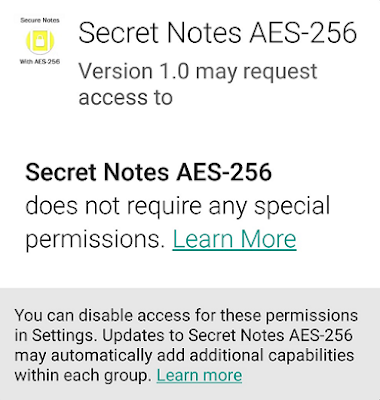 |
Secret Notes AES-256 Does Not Require Any Permission |
Usage:
To use, just download and enter a unique password (that you MUST remember), and then you can start typing your secret information. If you enter the password wrongly two times in a row, the application will default to a blank note list. This is for just in the case that you are forced to open the app. Uninstalling the application will automatically remove all the notes that the app stored on the phone. You can change your password anytime by using the "Change Password" setting in the App.
IMPORTANT 1: There is no way to retrieve the password if you cannot remember your password. Your password is not stored anywhere and by anyone. We will only be able to help you recover your notes if we have figured out a way to break AES-256, and we have NOT yet done so.
IMPORTANT 2: We will only support this app downloaded direct from Google Play. There are risks that the encryption may be weakened, malware infection, tracking logic added if you download the app from elsewhere.
IMPORTANT 3: Please use a more complex and hard to guess password to protect your notes. Yes, your birthday or phone number is easy to guess.
Features:
➤ No ADS and No root required
➤ Simple to use, no manual required
➤ Supports Smartphones, Tablets
➤ Supports Android KitKat, Lollipop, Marshmallow, Nougat
➤ Good resource management
➤ No frills, run with minimum RAM and CPU
➤ No unnecessary function in the app (to enhance security)
➤ No Android Permission required, zero, none, period
➤ Safe and Privacy focused, no servers and DOES NOT connect to the Internet
➤ Your notes will never leave your device
➤ Your notes is only stored in ENCRYPTED form, in the internal storage of your device
➤ Only your password (and pray you must not forget) can unlock your secret notes
➤ Backup of your notes is fully supported in the system
➤ No other app in the device can read your notes
➤ Check the permission required by other similar apps and you will agree that this is the BEST app for securing your notes in comparison
➤ You can request for full source code audit by contacting us
Download it now to secure your secrets.. We will refund with no questions if we fail in any one of our strengths. Have fun and God Bless.